Introducing

Know your adversary, know yourself, know your risk. Take your Continuous Threat Exposure Management to the next level.






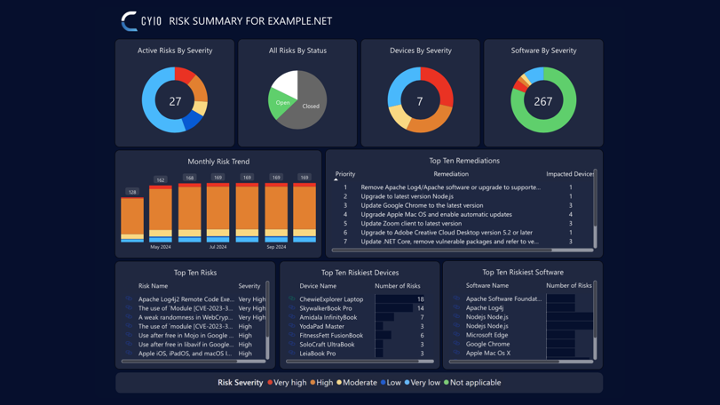
Ruthlessly Prioritize
Cyio, Latin for 'to-know', is the foundation for your Continuous Threat Exposure Management (CTEM) program. Gartner defines CTEM as "a program that surfaces and actively prioritizes whatever most threatens your business.” Most CTEM solutions offer a siloed view of your risks - sometimes from a vulnerability perspective or often from an attack surface perspective.
Cyio provides many perspectives - assets, adversaries, configurations, controls, business context, etc. The more variables you bring to the equation the better Cyio can prioritize risk and resources.
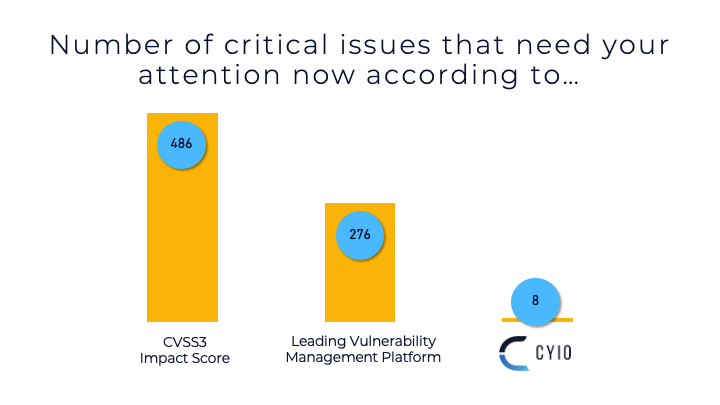
Applying vs Supplying Threat Intelligence...
See the difference when threat intel is applied to your environment vs just supplied. With Cyio, gain efficiency and confidence, not more sortable columns for the analyst to digest.
- Cyio continuously ingests results from your vulnerability and other assessment platforms to update risk statuses.
- Cyio continuously ingests threat intelligence and context about your environment.
- Cyio continuously applies new threat intelligence and context to reprioritize your risks at least daily.
Strengthen the “M” in
your CTEM program
- Address risks with Suggestions by Cyio and go beyond a single or automated remediation. Cyio suggests and accommodates multiple remediation paths, e.g., acceptance, transfer, mitigate, etc.
- Capture the who, what, when, and why for deviations (like accepting a risk and false-positives) with powerful auditing.
- Ensure the collaboration that your CTEM program requires with easily customized dashboards and assessment reports for a wide array of audience types.
- Take action directly from Cyio with mail handlers for ticketing and tasking systems. Apply a remediation or mitigation to one or more risks and send to Jira, ServiceNow, ConnectWise, Microsoft Teams, etc.
.gif?width=1920&height=1080&name=gggggg.pptx%20(1).gif)
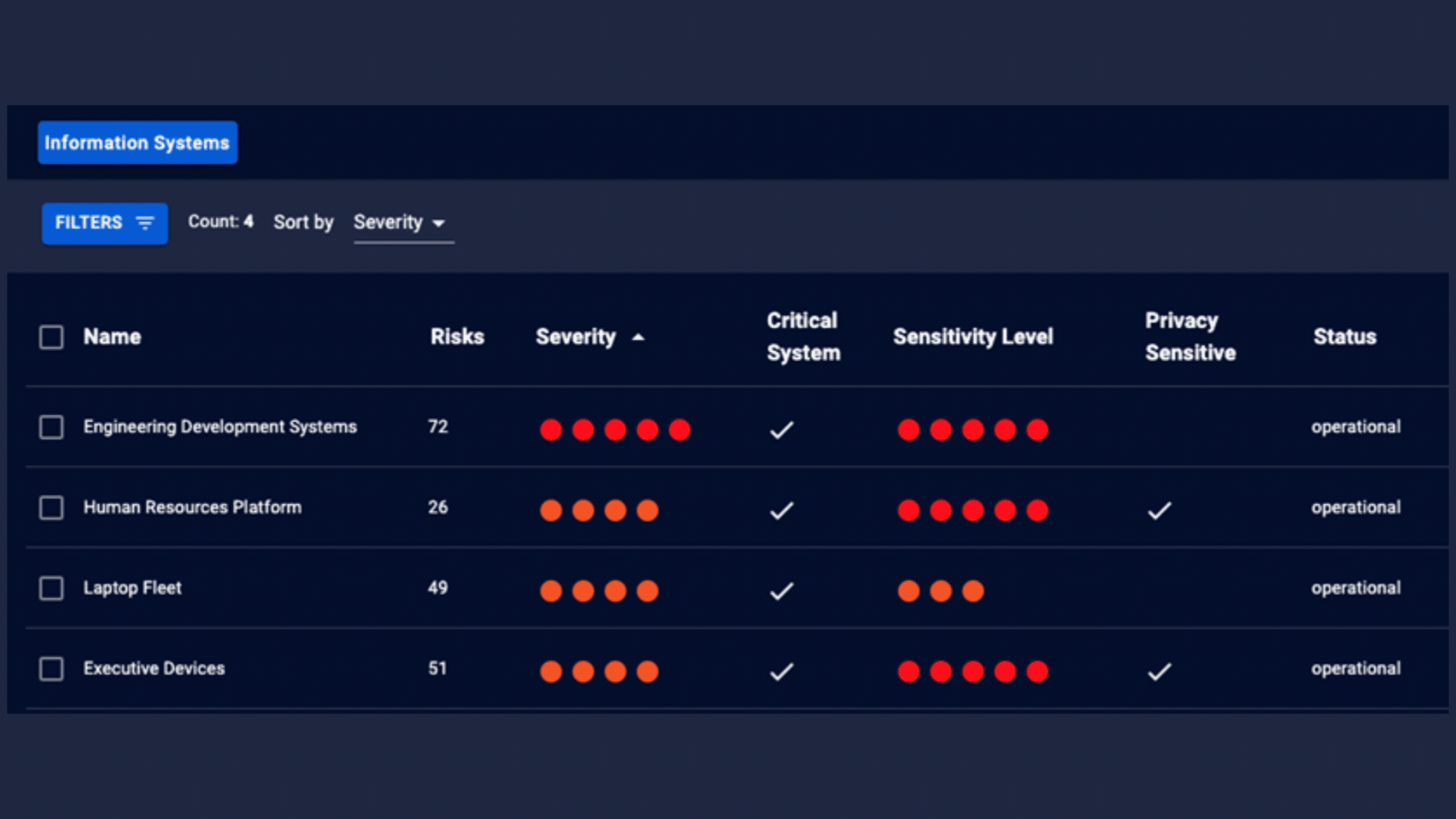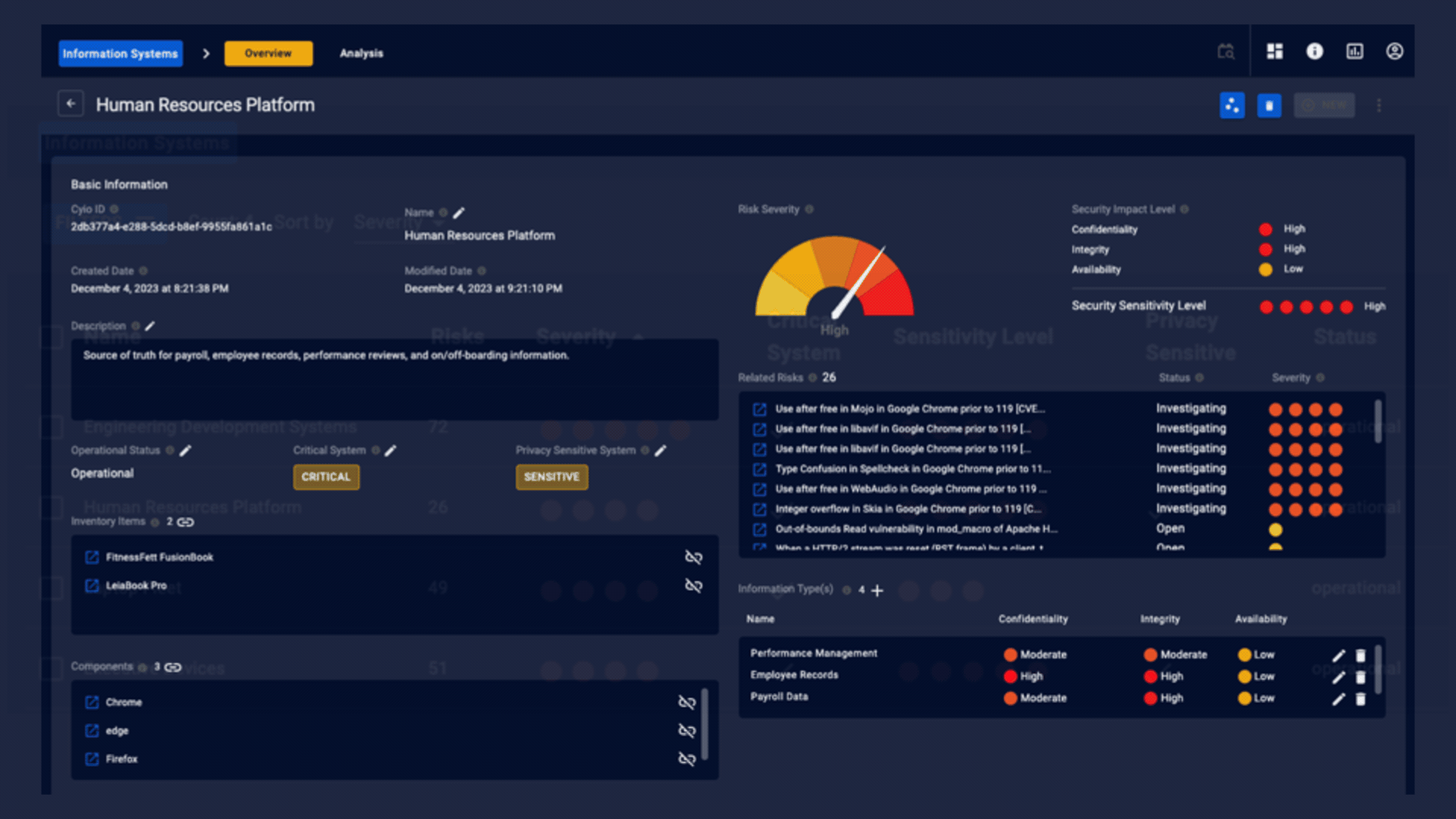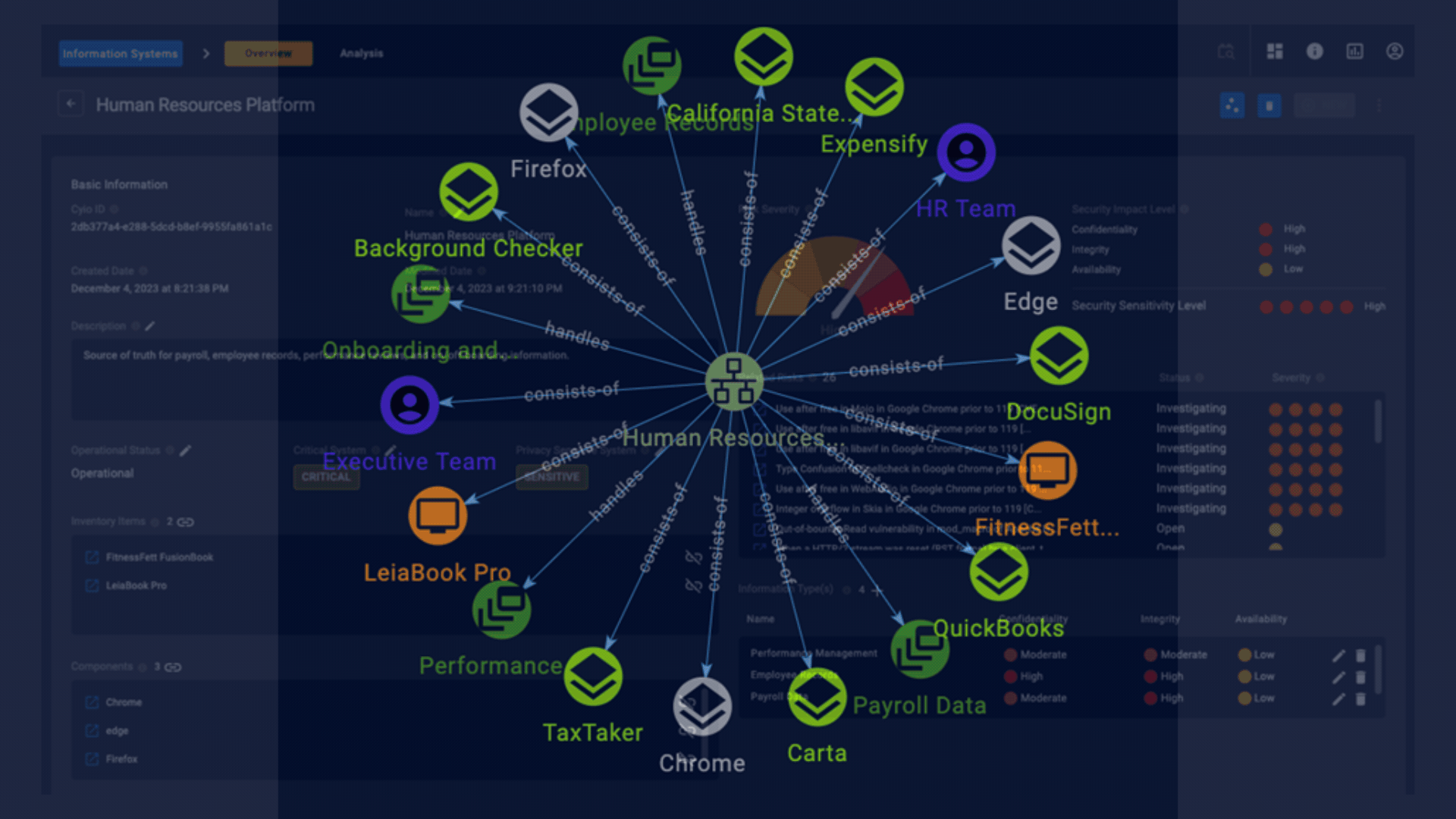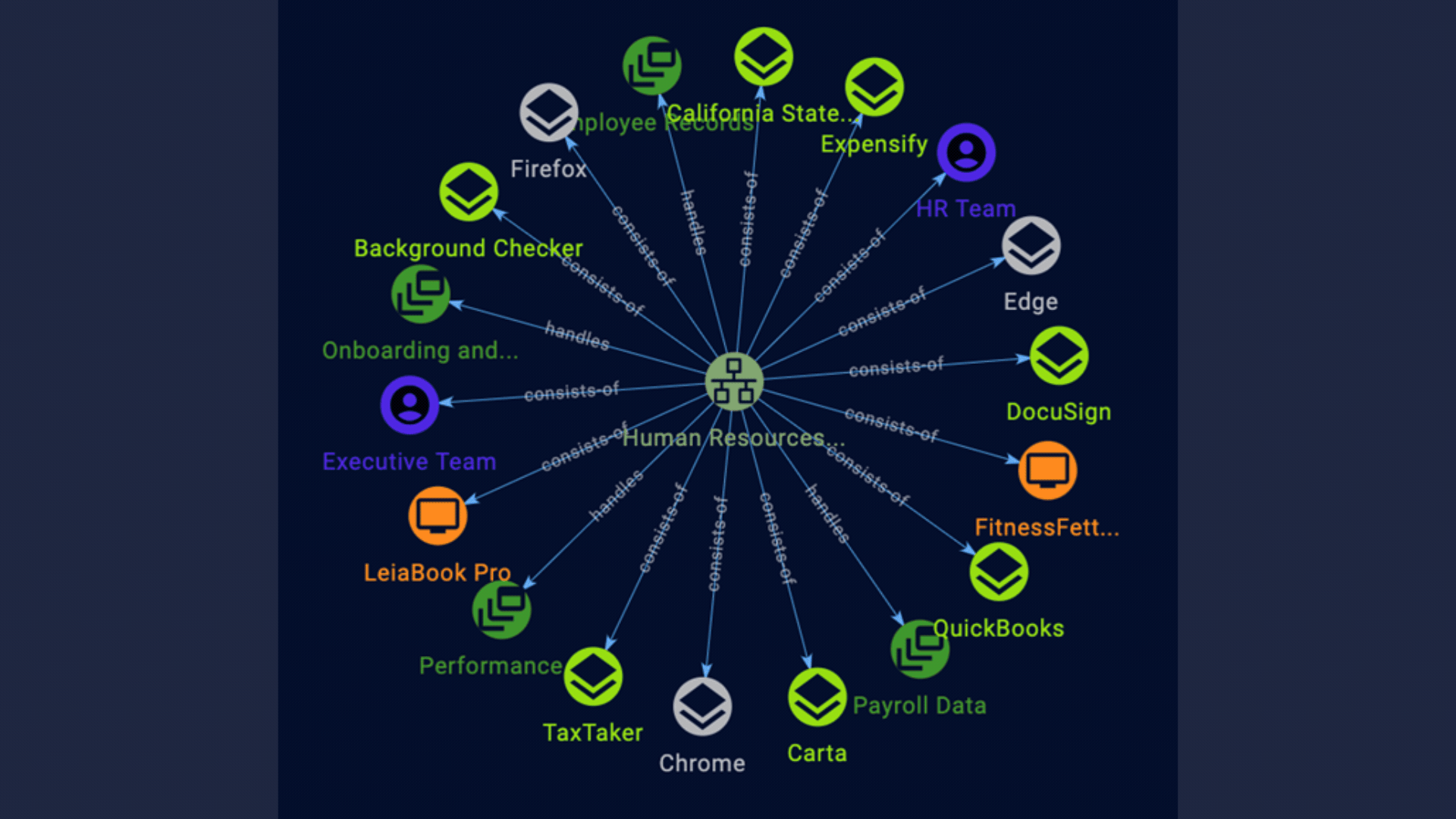
Visualize Business Functions
- Contextualize your environment based on business function with Cyio's information systems feature. Information Systems is a NIST term that is both one asset and a collection of assets. With Cyio, you can represent business capabilities by focusing on the types of information they collect, process, maintain, share, and more. Always standards-based, Cyio suggests tolerance levels for threats against the confidentiality, integrity, and availability of information that are part of these systems.
- Manage your prioritized risks across your enterprise, by device, by software, by network, or by information system. Navigate seamlessly among your risks, assets, and business capabilities with powerful hyperlinking.
Supported Integrations











